
Radware DefensePro x4420 Series
DDoS Protection and Attack Mitigation

Up to 50 Gbps throughput
Up to 100 Gbps throughput
Up to 160 Gbps throughput
Call a Specialist Today! 866-981-2998
Free Shipping! 


Click here to jump to more pricing!
DefensePro is a real-time, behavioral based attack mitigation device that protects your infrastructure against network & application downtime, application vulnerability exploitation, malware spread, network anomalies, information theft and other emerging cyber-attacks.
In today's info-security threat landscape, denial of service and distributed denial of service (DoS/DDoS) attacks are a major cause of network downtime. Whether executed by hacktivists to draw attention to a cause, fraudsters trying to illegally obtain data or funds, or a result of geo-political events, DDoS attacks are a destructive cyber weapon. Governments, utilities, financial services and commercial institutions face daily attacks.
Attacks are becoming more sophisticated and increasing in severity as they bypass traditional cloud and CDN protection services to target an organization's IT infrastructure and critical applications. The graph below from Radware's 2014-2015 Global Application & Network Security Report highlights a new trend: the rise of constant attacks against organizations.
The simplicity of launching cyber-attacks and variety of attack tools available are reasons why organizations suffer from increased attacks, such as DDoS. It is no longer about preventing attacks, but rather how to detect and mitigate them.
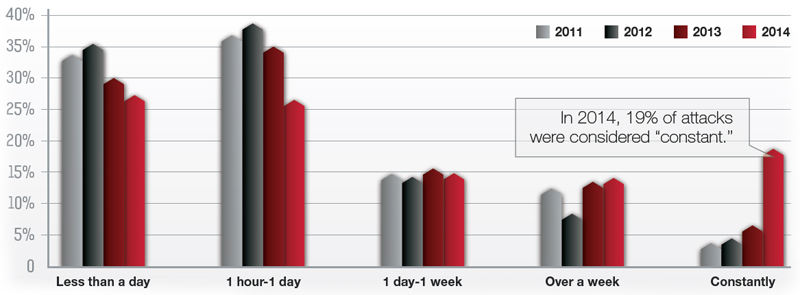
YoY Attack Durations
Cyber criminals don't keep regular hours. Instead, they work around the clock to find and exploit holes in your network. You need comprehensive enterprise network security designed to meet today's ever changing security challenges.
Enter Radware's DefensePro ― a real-time, behavioral based attack mitigation device that protects your infrastructure against network and application downtime, application vulnerability exploitation, malware spread, network anomalies, information theft and other emerging cyber-attacks.
DefensePro provides world-class security including distributed denial of service (DDoS) attack mitigation and SSL-based protection to fully protect applications and networks against known and emerging network security threats such denial of service attacks, DDoS attacks, Internet pipe saturation, attacks on login pages, attacks behind CDNs, and SSL-based flood attacks with:
![]()
Dedicated Hardware That Protects Without Impacting Legitimate Traffic
DefensePro uses a dedicated hardware platform based on Radware's OnDemand Switch supporting network throughputs up to 40Gbps. It embeds two unique and dedicated hardware components: a DoS Mitigation Engine (DME) to prevent high volume denial of service attacks and DDoS attacks, flood attacks, without impacting legitimate traffic, and a StringMatch Engine (SME) to accelerate signature detection
![]()
Centralized Attack Management, Monitoring and Reporting
APSolute Vision offers a centralized attack management, monitoring and reporting solution across multiple DefensePro devices and locations. It provides the user real-time identification, prioritization and response to policy breaches, cyber-attacks and insider threats
![]()
Complete Set of Security Modules
Intrusion Prevention System (IPS), Network Behavioral Analysis (NBA), anti-DDoS/Denial-of-Service (DoS) Protection, Reputation Engine and SSL Attack Protection. It employs multiple detection & mitigation modules including adaptive behavioral analysis and challenge response technologies in addition to signature detection.
![]()
The Accuracy of Inline, the Scalability of Out of Path
DefensePro devices can be deployed inline or out-of-path (OOP) in a scrubbing center to provide the highest mitigation accuracy within the shortest time.
Based on standard signature detection technology to prevent the known application vulnerabilities, DefensePro consists of patent protected behavioral based real-time signatures technology that detects and mitigates emerging network attacks in real time such as zero-minute attacks, DoS/DDoS attacks and application misuse attacks ― all without the need for human intervention and without blocking legitimate user traffic.
DefensePro is a core part of Radware's next generation Attack Mitigation System (AMS) a set of patented technologies designed for the most advanced internet-borne cyber-attacks. AMS extends the "network" of attack detection and mitigation capabilities beyond the data center for:
![]()
Cloud- hosted business services and applications
![]()
Tools, servers and applications need protection within a virtualized environment
![]()
Mobile work force increasingly depend on remote access to internal business applications and SaaS
![]()
Advanced detection and mitigation techniques need to be ported to tomorrows open network fabrics
DefensePro includes a comprehensive set of four essential security modules – anti-DDoS, network behavioral analysis (NBA), intrusion prevention system (IPS) and SSL attack protection (DefenseSSL) - to fully protect the application infrastructure against known and emerging network security attacks. It employs multiple detection and mitigation modules including adaptive behavioral analysis, challenge response technologies and signature detection.
Compared to stand-alone solutions, the synergy of multiple security modules on a single, hardware-accelerated platform enables more effective protection against attackers who seek to systematically compromise business assets while providing unified reporting, forensics and compliance.
DefensePro consists of patent protected, adaptive, behavioral-based real-time signature technology that detects and mitigates emerging network attacks, zero-minute, DoS/DDoS, application misuse attacks, network scanning and malware spread. It eliminates the need for human intervention and does not block legitimate user traffic.
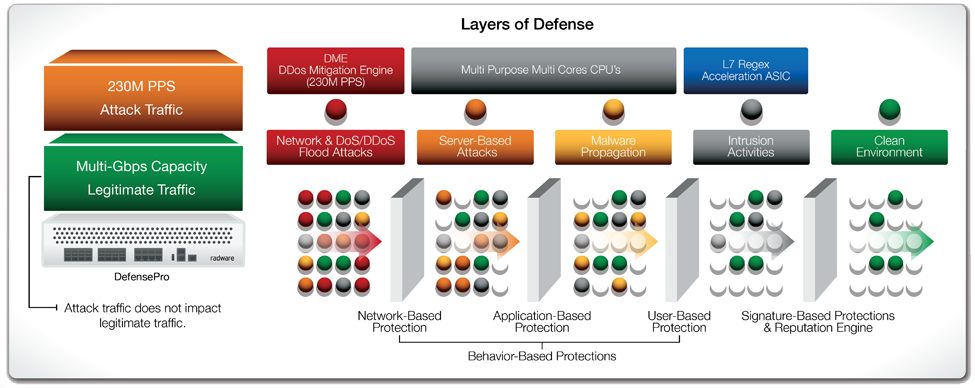
DefensePro Architecture
Radware DefensePro is a network intrusion prevention solution used for DDoS protection and SSL-based attack protection.
With the proper DoS protection system in place, organizations no longer need to be concerned with the possibility of network disruptions. DoS attacks flood a network with excessive amounts of traffic for the sole purpose of causing network damage.
| Features | Benefits |
|---|---|
| Maintain Business Continuity of Operations (COOP) Even When the Network is Under Attack |
|
| Security Solutions for Data Centers in a Single Box |
|
| Best-in-class Unified Monitoring and Reporting Solution |
|
| Reduce Total Cost of Ownership (TCO) of Security Management |
|
| Maintain Business Continuity and Productivity While Gaining DDoS Protection |
|
| Accurate Attack Prevention |
|
| Comprehensive protection and high performance with a single platform for carriers, cloud providers, large e-commerce and online businesses |
|
| High Performance |
|
| "Pay-As-You-Grow" for Reduced CAPEX |
|
| Ease of Security Management for Reduced OPEX |
|
Emerging Network Threats Require Multiple Protection Tools to Secure Your Business
Data center and network security managers face an increasing threat landscape including: application vulnerabilities; authentication defeat; information theft; malware spread; network and application downtime; Trojans and more. In order to combat the increasing threat landscape security managers are required to deploy multiple detection and protection tools including: intrusion prevention systems (IPS), denial-of-service (DoS) protection and network behavioral analysis (NBA) and reputation services.
Recent attacks in 2009 and 2010 such as the July 2009 cyber attacks and Confi cker malware have left many organizations vulnerable to Botnet attacks, zero-minute attacks and more – even when deploying one of these tools. The conclusion is that there is no single tool that can handle today’s emerging network attacks – until now.
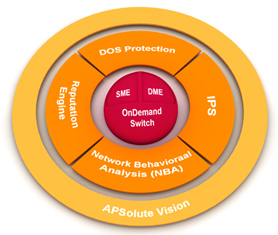 APSolute Attack Prevention with DefensePro: Protect Your Application Infrastructure against Known and Emerging Network Threats in Real-Time
APSolute Attack Prevention with DefensePro: Protect Your Application Infrastructure against Known and Emerging Network Threats in Real-TimeRadware’s award-winning DefensePro is a real-time network attack prevention device that protects your application infrastructure against network and application downtime, application vulnerability exploitation, malware spread, Information theft and other emerging network attacks.
The synergy of multiple protection modules on the same platform enables more effective protection against attackers who seek to compromise the business assets systematically when compared to stand alone solutions deployment, while providing unifi ed reporting and compliance.
APSolute Vision™ accompanies our DefensePro APSolute attack prevention with an enterprise-wide view of security and compliance status from a single console. Data from multiple devices is collected and evaluated in a consolidated view of dashboards and reports. These views provide extensive yet simple drilldown capabilities that allow users to easily drill into information to speed incident identifi cation and provide root cause analyses, improving collaboration between network operations center (NOC) and security operations center (SOC) teams, while accelerating the resolution of security incidents.
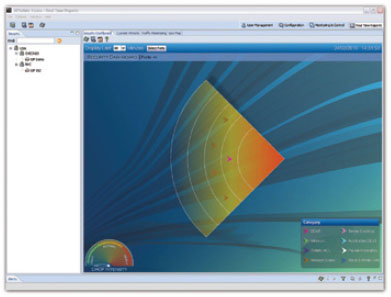
The real time sonar view allows you to see current attacks in your network. High risk attacks are
located closer to the sonar transmitter. The side meter indicates the drop intensity of attack traffic.
Maintain business Continuity of Operations (COOP) even when the network is under attack
Best security solution for data centers in a single box
Most accurate attack detection and prevention
Best in class unified monitoring and reporting solution
Reduces total cost of ownership (TCO) of security management
DefensePro devices can be deployed inline, out-of-path (OOP) or in a scrubbing center to provide the highest mitigation accuracy within the shortest time. Each deployment mode offers the same performance as an inline device.
With DefensePro deployed either inline or out-of-path as well as in a scrubbing center, the devices are able to communicate with each other in real-time to collect automatic updates of normal traffic baselines, detect behavioral patterns and obtain attack footprints. This constant real-time flow of defense messaging enables DefensePro to provide accurate and instant mitigation without the need to learn this information when an attack occurs.
Deploying DefensePro devices out of path or in a scrubbing center is the most scalable and flexible solution as it is based on the maximum attack mitigation capacity needed, without being limited by the actual network physical topology.
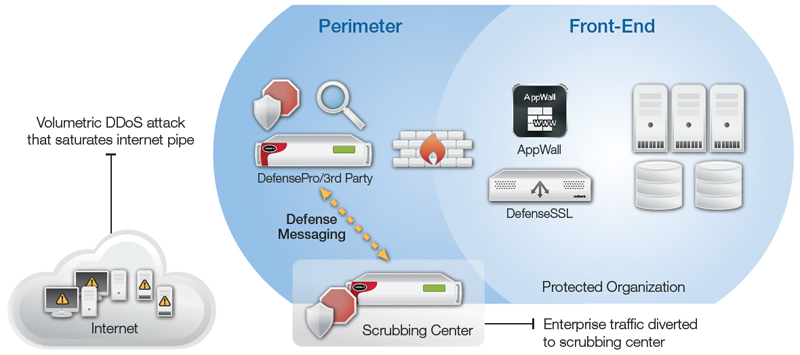
DefensePro device deployed inline in the enterprise perimeter to detect/mitigate attacks in real-time;
scrubbing center invoked for mitigation of volumetric attacks that threaten to saturate the internet link.
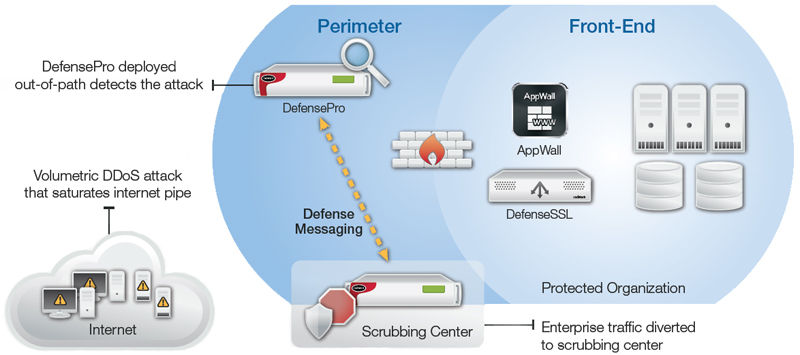
DefensePro deployed out-of-path for attack detection; suspicious traffic is diverted
to the deployment with scrubbing center for attack mitigation.
In addition to the security modules integrated in DefensePro, Radware's attack mitigation solution includes an SSL decryption/encryption engine, a WAF module and a cloud based attack mitigation scrubbing service that works in sync with the on premise solution. With no performance impact or risk, Radware's attack mitigation solution ensures business continuity even when under attack.
The solution is enhanced with a central Security Information Event Management (SIEM) to provide unified situational awareness and Radware's Emergency Response Team (ERT) offering of 24/7 security expert support for customers under attack in real time to mitigate attacks and restore operational status.
Unique messaging assures that each component provides information about traffic baselines and real-time signatures to the others, so that all system components have full visibility into all information.
Through this messaging, Radware's attack mitigation solution can detect attacks where it should and mitigate attacks where it's best. For example, the system can detect a volumetric attack at the network perimeter but mitigate it in the cloud. This automatic, real-time feature enables organizations to scale the mitigation capabilities of the solution by moving mitigation as far as possible from the application infrastructure.
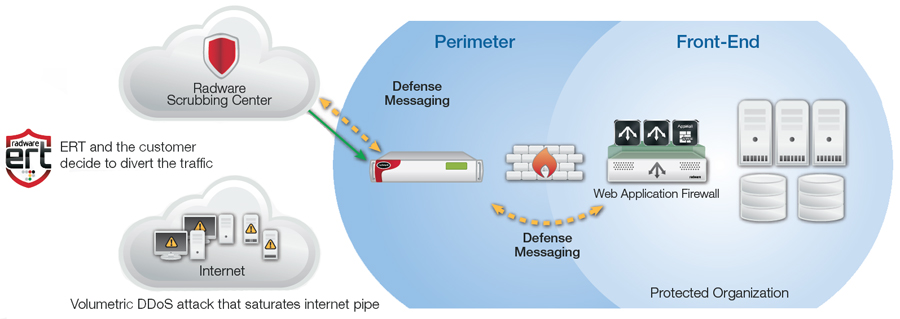
Complete Attack Mitigation Solution Deployment
Radware's award-winning IPS and DoS solution for protecting against emerging network attacks in addition to known, vulnerability-based attacks.
![]()
DefensePro x06 Series
Designed for small to medium sized data centers protection and Internet Gateway
![]()
DefensePro x016 Series
Designed for medium sized data centers protection deployed by large enterprises, eCommerce and service providers

DefensePro x412 Series
Designed for large data centers protection deployed by large enterprises, eCommerce and service providers
DefensePro x420 Series
Designed for large data centers protection deployed by large enterprises, eCommerce and service providers

DefensePro x4420 Series
Designed for:
| Features | x06 Series | x016 Series | x412 Series | x420 Series | x4420 Series |
|---|---|---|---|---|---|
| Hardware Platform | OnDemand Switch VL S1
(single PS) OnDemand Switch VL S2 (dual PS) |
OnDemand Switch 2 S1
(single PS) OnDemand Switch 2 S2 (dual PS) |
OnDemand Switch 3 S1 (Behavioral Protection) OnDemand Switch 3 S2 (IPS & Behavioral Protection) |
OnDemand Switch HTQ | OnDemand Switch HTQe |
| Performance | |||||
| OnDemand Scalable Throughput Licenses1 | DP model 206 - 200 Mbps DP model 506 - 500 Mbps DP model 1006 - 1 Gbps DP model 2006 - 2 Gbps |
DP model 1016 - 1 Gbps DP model 2016 - 2 Gbps DP model 3016 - 3 Gbps |
DP model 2412 - 2 Gbps DP model 4412 - 4 Gbps DP model 8412 - 8 Gbps DP model 12412 - 12 Gbps |
DP model 10420 - 10 Gbps DP model 20420 - 20 Gbps DP model 30420 - 30 Gbps DP model 40420 - 40 Gbps |
DP model 504420 – 50 Gbps DP model 1004420 – 100 Gbps DP model 1604420 - 160 Gbps |
| Max Mitigation Capacity/Throughput | 3Gbps | 3Gbps | 18Gbps | 60Gbps | 300Gbps |
| Max Concurrent Sessions | 2,000,000 | 2,000,000 | 4,000,000 | 6,000,000 | 25,000,000 |
| Maximum DDoS Flood Attack Prevention Rate | 1,000,000 pps | 1,000,000 pps | 10,000,000 pps | 25,000,000 pps | 230,000,000 pps |
| Latency | < 60 micro seconds |
||||
| Real-time Signatures | Detect and protect attacks in less than 18 seconds |
||||
| Inspection Ports | |||||
| 10/100/1000 Copper Ethernet | 4 | 12 | 8 | - | - |
| 1 GE | 2 (SFP) | 4 (SFP) | 4 (SFP) | 20 (SFP+) | 20 (SFP+) |
| 10 GE | - | - | 4 (XFP) | 20 (SFP+) | 20 (SFP+) |
| 40 GE | - | - | - | 4 (QSFP+) | 4 (QSFP+) |
| 100 GE | - | - | - | - | 4 (QSFP28) |
| Management Ports | |||||
| 10/100/1000 Copper Ethernet | 2 | 2 | 2 | 2 | 2 |
| RS-232 | RJ-45 | RS-232 | RS-232 | RJ-45 | RJ-45 |
| Mode of Operation | |||||
| Network Operation | Transparent L2 Forwarding | Transparent L2 Forwarding/IP Forwarding | |||
| Deployment Modes | In-line; SPAN Port Monitoring; Copy Port Monitoring; local out-of-path; Out-of-path mitigation (scrubbing center solution) | ||||
| Tunneling Protocol | VLAN Tagging, L2TP, MPLS, GRE, GTP, IPinIP | ||||
| IPv6 | Yes | ||||
| Jumbo Frame | Supported | ||||
| Block Actions | Drop packet, reset (source, destination, both), suspend (source, src port, destination, dest port or any combination), Challenge-Response for TCP, HTTP and DNS suspicious traffic | ||||
| High Availability | |||||
| Fail open/fail-close2 | Internal fail-open/fail-close for copper ports, Internal fail-close for fiber ports | ||||
| Dual Power Supply | Optional, hot swappable | Yes, hot swappable | |||
| Advanced internal overload mechanism3 | Yes | Yes | Yes | Yes | Yes |
| Active-passive cluster | Yes | Yes | Yes | Yes | Yes |
| Physical | |||||
| Dimensions (W x D x H) mm | 424 x 457 x 44 mm (1U) | 424 x 600 x 44 mm (1U) Dual PS: 424 x 600 x 88 mm (2U) |
424 x 600 x 88 mm (2U) | 424 x 537 x 88 mm (2U) EIA Rack or Standalone: 482 mm (19 in) |
424 x 600 x 88 mm (2U) EIA Rack or Standalone: 482 mm (19 in) |
| Weight | Single PS: 7.2 kg (15.9 lbs) Dual PS:8.7 kg (19.2 lbs) |
Single PS: 9.5 kg (20.9 lbs) Dual PS: 10.9 kg (24.0 lbs) |
18.0 kg (39.0 lbs) | 15.1 kg (33.2 lbs) | 18.7 kg (41.2 lbs) |
| Power Supply (Auto-range) | AC: 100-120V/200-240V,
47-63 Hz DC: -36 – -72V |
AC: 100-120V/200-240V, 47-63 Hz DC: -36 – -72V |
AC: 100-120V/200-240V,
47-63 Hz DC: -36 – -72V |
AC: 100-120V/200-240V, 47-63
Hz DC: -36 – -72V |
|
| Power Consumption | Single PS: 177W Dual PS: 147W |
Single PS: 302W Dual PS: 312W |
OnDemand Switch 3 S1
-451W OnDemand Switch 3 S2 -476W |
634W | 890W |
| Heat Dissipation (BTU/h) | Single PS: 604 BTU/h Dual PS: 501 BTU/h |
Single PS: 1029 BTU/h Dual PS: 1064 BTU/h |
OnDemand Switch 3 S1 -
1538 BTU/h OnDemand Switch 3 S2 - 1623 BTU/h |
2162 BTU/h | 2930 BTU/h |
| Operating Temperature | 0-40°C (32-104°F) | ||||
| Humidity | 5% to 95% (non-condensing) | ||||
| Safety Certifications | CE LVD( EN 60950-1), CB - IEC 60950-1, CCC, cTUVus, AS/NZS 60950.1 | ||||
| EMC | CE EMC (EU directive 2004/108/EC), FCC Part 15B Class A, ICES-003, VCCI, C-TICK | ||||
| Other Certifications | RoHS Compliant (EU directive 2011/65/EU) | ||||
| Warranty | 1-year hardware and software maintenance | ||||
| Support | Certainty Support Program | ||||
1 Throughput is measured at the egress of the DP and includes only legitimate traffic (Dropped packets are not calculated in the license).
2 External fiber fail-open switch with SFP ports is available at additional cost.
3 Overload mechanism is designed to obtain maximum security coverage under extreme traffic loads.
Download the Radware DefensePro Datasheet (PDF).
Download the Radware DefensePro Technical Specifications Datasheet (PDF).