 Radware DefenseFlow
Radware DefenseFlow
NetFlow and SDN based DDoS Attack Defense

Click here to jump to more pricing!
Overview:
Radware's DefenseFlow Software Defined Networking (SDN) application allows organizations to dynamically mitigate Network, Application and APT attacks utilizing the entire network capacity.
New security threats to telecommunications providers and enterprises require rapid provisioning of security protection solutions capable of identifying and blocking unknown attacks at unknown scale. Radware DefenseFlow is an SDN Based Adaptive Attack Mitigation solution offering the ability to dramatically accelerate security capability provisioning time while automatically integrating into diverse and large scale networks.
What Does DefenseFlow Do?
DefenseFlow is a network-wide DDoS attack detection and cyber command and control application designed to protect networks against known and emerging network attacks that threaten network resource availability. DefenseFlow supports traditional NetFlow and emerging software defined networks (SDN)/OpenFlow networks. Coupled with DefensePro, DefenseFlow enables carriers, Internet Service Providers (ISP) and cloud service providers to ensure service availability by removing network and application DDoS attacks.
DefenseFlow Use Cases
Radware offers three use cases with DefenseFlow attack detection and cyber control and command along with DefensePro for out of path DDoS attack defense and mitigation:
![]()
NetFlow-based attack detection
One stop shop attack detection and mitigation solution including NetFlow collector, attack detection, attack life cycle management and DDoS attack mitigation solution.
![]()
3rd party NetFlow-based attack detection
Integrating with existing third party NetFlow-based attack detection solutions, attack life cycle management and DDoS attack mitigation solution.
![]()
OpenFlow-based attack detection (SDN)
One stop shop DDoS attack detection and mitigation solution for SDN-enabled networks including OpenFlow based attack detection, attack life cycle management and attack mitigation solution.
What Makes DefenseFlow a Better DDoS Attack Defense Solution?
Best Quality-of-Mitigation Solution in the Industry
DefensePro devices deployed at the carrier scrubbing center offers the following features.
- Widest attack coverage - mitigate all type of DoS/DDoS attacks in seconds (e.g. application and network level)
- Highest mitigation accuracy - block attack traffic without blocking legitimate user traffic
- Save on SOC costs involved by handling attack leakage and false-positives
Best Quality-of-Detection DDoS Detection Solution
DefenseFlow features patent protected behavioral-based detection engine that detects DDoS attacks in real-time and diverts attack traffic to the scrubbing center.
- Detects all types of network DoS/DDoS attacks in seconds including zero-day attacks; best time to detect in the industry
- Lowest false detection rate in the industry due to rate and rate-invariant multi-parameters detection engine
- Significant cost savings of SOC operations through automation – saving SOC resources involved in analyzing attack alerts and manual traffic diversion to the scrubbing center
Suitable for the Current and Future Carrier Environment
Investment protection due to DefenseFlow solution that supports both NetFlow and software defined networks (SDN).
- DefenseFlow fully integrates with existing NetFlow based traffic monitoring and DDoS attack detection tools
- DefenseFlow offers seamless transition to evolving SDN technologies by fully supporting standard and proprietary SDN controllers for DDoS attack defense and traffic diversion
Features and Benefits:
Software Defined Networking Application & DDoS Protection Services
Built as a native SDN application, Radware's DefenseFlow provides DDoS protection services and equips network operators with the following key advantages when adding DDoS protection into their infrastructure:
- Unprecedented coverage against all type of network DDoS attacks
- Best design for attack mitigation – attack detection is always performed out of path; during attack period only suspicious traffic is diverted through the mitigation device
- Most scalable mitigation solution – DefensePro mitigation devices can be placed in any location, DefenseFlow diverts the traffic to the nearest mitigation device
Legacy DDoS protection services that make use of scrubbing centers are costly because they need hardware detectors in every network location, BGP for traffic diversion, and GRE tunnels to forward the traffic to its designated network object. With SDN, a DDoS protection solution turns into a software application that adds intelligence to the network. There is no need for additional hardware, BGP or GRE operations, which is a great cost reduction opportunity for operators.
Solution:
DefenseFlow uniquely addresses the new requirements by leveraging the programmable and dynamic nature of software defined networks and by employing adaptive security algorithms combining the following capabilities:
(1) Uniquely identify network level, application level & APT attacks,
(2) Instantaneously provision security capabilities throughout the network and
(3) Distribute the attack mitigation functionality leveraging the entire SDN capacity.
While alternative approaches require static provisioning of security systems throughout the network and sized according to the protected network capacity, DefenseFlow leverages the entire network combined with ondemand intelligence of network, application and APT recognition algorithms, by using only the exact amount of resources needed, at the optimal network location in order to identify and block various attacks at various sizes.
The solution operates using a continuous 4 stage service lifecycle:
- Provision Security detection throughout the network by programming counters throughout the SDN nodes, by provisioning L4-7 Application Intelligence (AI) engines & by mirroring traffic to the L4-7 AI engines.
- Collect information from the entire set of provisioned information sources.
- Analyze network and application information in order to categorize behavioral patterns, maintain an ongoing behavioral baseline and identify any steep deviations from the baseline.
- Control traffic and service elements by blocking traffic, diverting traffic to dedicated attack mitigation engines and optimizing security policies.
The solution is an evolution of the DefenseFlow Network Behavioral Analysis (NBA) solution, adding to it an Application Behavioral Analytics (ABA) Component as well as an Advanced Persistent Threat (APT) Detection Module. In order to formulate a consistent and actionable behavioral baseline, and identify deviations from this baseline at the application behavior and APT levels, several implementations of patented behavioral analysis mechanisms are used. These mechanisms define real-time application and network attack signatures most effective against modern zero-day attacks. Furthermore, the ability to scale intelligent application level attack detection engines on the fly and distribute traffic across these engines intelligently (leveraging SDN) is pending patent under the Radware ElasticScale network services framework.
The illustration outlines various capabilities of the DefenseFlow solution by showing the following elements:
- User & Server networks, these are organizationally controlled assets under which the SDN is assumed to operate (fully or partially) for collecting traffic statistics, mirroring traffic to vDPI engines & blocking traffic.
- Edge network through which all traffic in and out of the organization passes; this network section is assumed to be fully SDN capable and is responsible for collecting traffic statistics, mirroring traffic to vDPI engines, diverting Traffic to Attack Mitigation systems & blocking traffic.
- The L4-7 Service fabric which is pictured as a single area, but can be distributed throughout the entire SDN as best suited to protect the network. The fabric consists of L4-7 systems such as DPI engines, attack mitigation systems etc. the DPI engines are responsible to collect Application layer meta-data and statistics and the Attack mitigation systems are responsible to block attacks at very high certainty.
- The solution control plane consists of the SDN controller and DefenseFlow applications and is responsible for programming the network to: collect network statistics, intelligently mirror traffic to vDPI elements, Divert suspicious traffic to Attack mitigation systems and block malicious traffic at most appropriate network locations.
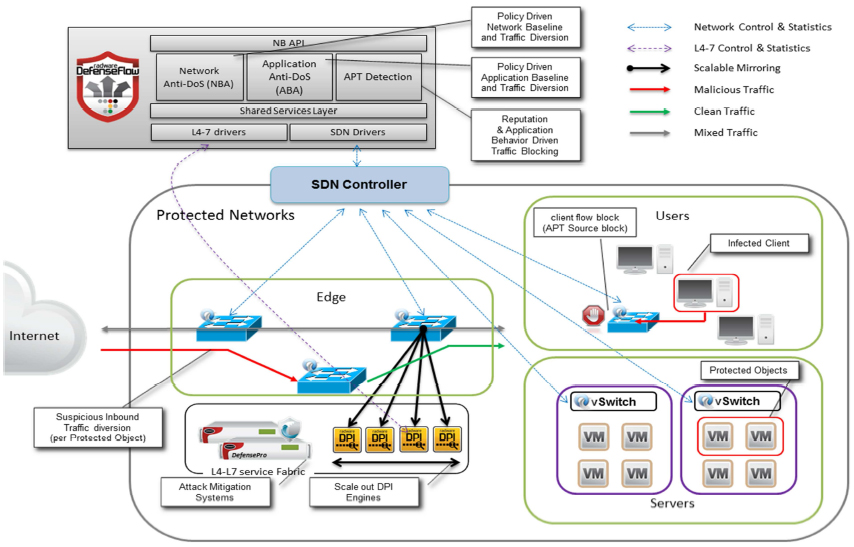
DefenseFlow – Distributed Attack Detection, Traffic Diversion & Attack Mitigation
Summary
The DefenseFlow Adaptive Network, Application and APT Protection solution leverages the field proven Radware Attack Mitigation System mechanisms, in form of an SDN application, together with SDN to enable cost effective and scalable Attack Mitigation capabilities for organizations. The solution addresses a broad range of security threats from network DDoS through Application DDoS to APT offering organizations one of the most cost effective solutions to mitigate organizational risk.
DefenseFlow is a perfect example of how SDN changes existing network service architectures to employ a collaborative mechanism in which network and L4-7 systems interact and increase value to end user. This is done by changing the network role from hosting services - to being part of the service - in this case offering increased security protection. DefenseFlow is the only solution that addresses the dynamic nature (unknown type and scale) of Attacks and brings the dynamic capabilities of SDN to mitigate the associated risks. Furthermore, as opposed to other available solutions that offer new API's to program existing systems. DefenseFlow is a clear showcase of how SDN offers immediate value to organizations that run business critical networks.
Technical Specifications:
| DefenseFlow Out-of-Path Network DDoS Protection | |
|---|---|
| Attacks Detection | |
| Type of attacks detected |
|
| Detection methods |
|
| Security Policy Settings | |
| Protected object - supported network classification per policy |
|
| Number of protected objects supported per DefenseFlow application | 500 |
| Management & Monitoring | |
| Configuration management interface | REST API, CLI and Web UI |
| Security logs interface | Web UI |
| Security logs sources | Collected from DefenseFlow and DefensePro mitigation devices to provide unified event log view |
| Real-time traffic monitoring statistic interface | Web UI |
| Out-of-Path Deployment | |
| Number of supported Radware's DefensePro mitigation devices | 10 |
| Protected object baseline synchronization with Radware's DefensePro mitigation device | Automatic |
| Policy synchronization with Radware's DefensePro device | Automatic |
| "Short" Traffic Redirection | One hop traffic redirection |
| Traffic redirection to local mitigation device | Supported for both SDN and BGP redirection |
| Traffic redirection granularity | Suspected traffic type per protected object |
| Short traffic redirection modes | Ingress only |
| "Long" Traffic Redirection | Traffic redirection to a remote mitigation device (scrubbing center) connected anywhere in the network |
| Traffic redirection to remote mitigation device | Supported for both SDN and BGP redirection |
| Traffic redirection granularity | Suspected traffic type per protected object |
| Attack Mitigation | |
| DP Mitigation device version | DefensePro version 7.4x |
| Clustering of DP mitigation devices | Yes |
| Environment Compatibility | |
| SDN controllers support | ALU SAM, Cisco OSC |
| xFlow statistics collectors support | Radware's Flow collector |
| External detectors | Pluggable API to 3rd party detectors |
| Software Specifications | |
| Supported environments | Install package for general purpose server, VMware ESXi 5.x |
| Software package | Includes installation of Vision management system on single platform |
| Minimal Requirements for General Purpose Server | |
| Processor | 8 CPUs |
| Memory | 24 GB |
| Hard drive | 500 GB |
| Network connectivity | 4 NICs |
| Minimal Requirements for VA over VMware ESXi 5.x | |
| Memory | 8 GB |
| Hard drive | 50 GB |
Documentation:
Download the Radware DefenseFlow Datasheet (PDF).
Download the Radware DefenseFlow Technical Specifications Datasheet (PDF).

